Maximum Security
In a hyper-connected world, organisations are facing ever-increasing cybersecurity threats. Cyber-attacks, data leaks and system vulnerabilities are becoming a major concern for those looking to protect their digital assets. It is in this context that the Vulnerability Operations Centre (VOC) acts as a key pillar of proactive defence against these risks.
What is a VOC ?
“The VOC is to offensive security what the SOC is to defensive security”
YOGOSHA
A VOC is a specialist structure that excels at identifying, managing and reducing security vulnerabilities in an organisation’s IT systems. Unlike the Security Operations Centre (SOC), which focuses on real-time monitoring of security incidents, the VOC takes a proactive approach: it detects potential risks before they can be exploited.
As the security hub, the VOC coordinates and prioritises actions to identify and address vulnerabilities in technological infrastructures. Through continuous monitoring, close collaboration between security and development teams, and the use of advanced tools, the VOC anticipates threats and thus strengthens the defence of the company’s digital assets.
The design of a Vulnerability Operations Centre (VOC) is based on an in-depth analysis of cyber exposure to protect information systems. The VOC focuses on the identification and management of critical assets, such as SPOFs (Single Points of Failure), as well as the analysis of vulnerability exploitation scenarios that the company considers to be highly critical to business continuity.
The VOC’s primary mission is to mitigate cyber risk by identifying vulnerabilities that could be exploited and quickly implementing corrective actions. This objective is part of the overall strategy to secure the organisation’s information systems. By strengthening the resilience of critical infrastructure, protecting sensitive data and ensuring the availability of essential services, the VOC actively contributes to maintaining a secure and reliable digital environment for business.
The proactive management of these risks, combined with the remediation of identified vulnerabilities, is a strategic challenge for any organisation seeking to minimise the impact of cyber threats and ensure business continuity.
Vulnerability management cycles are based on principles common to different security standards. However, the approaches and processes may vary depending on the standards or norms followed (such as ISO 27001, NIST, CIS or PCI DSS). In general, the key stages remain similar, although their formalisation or level of detail may vary from one standard to another.
Key roles of the VOC in the vulnerability management process
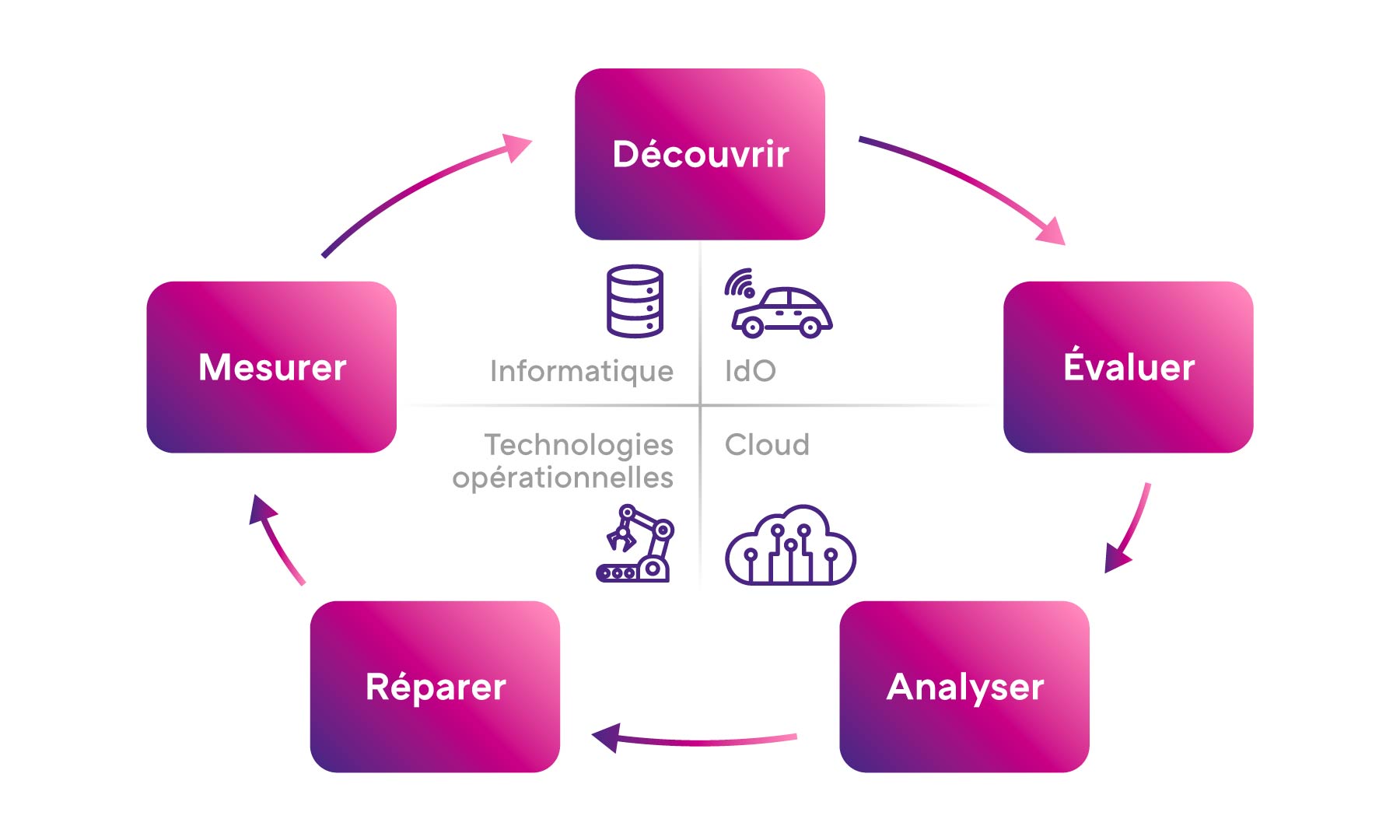
1. Risk detection: The VOC relies on scanning, automated analysis and continuous monitoring tools to identify weaknesses in information systems, including outdated software, incorrect configurations or new vulnerabilities discovered in the cybersecurity community.
- Implementation of detection rules
The implementation of detection rules consists of defining in the monitoring tool the perimeters in which network traffic must be captured, as well as those that require specific scans to enhance security or apply appropriate rules, particularly in sensitive sectors such as banking. This includes identifying assets not listed in the CMDB that may be indicators of compromise to the SOC (orphan asset detection), as well as managing the attack surface and exposed sources.
- Optimisation of vulnerability management through asset inventory
Asset inventory is critical to effective vulnerability management because it provides a clear and detailed view of the infrastructure that needs to be protected. By cataloguing all active elements (servers, applications, devices), it becomes easier to prioritise patches, identify critical systems exposed to threats, and monitor the evolution of vulnerabilities over time. This inventory also allows the professions to define the criticality of their assets according to the CIA criteria (Confidentiality, Integrity, Availability), which facilitates the prioritisation of actions for the VOC and a more precise qualification of vulnerabilities. It also enables the professions to better monitor changes within their perimeter (change of asset manager, addition of ancillary buildings, removal of assets), thus reducing the VOC’s workload in terms of time, resources and vulnerability management.
2. Risk assessment : Once vulnerabilities have been identified, the VOC assesses their criticality according to their potential impact on the organisation. This stage consists of prioritising vulnerabilities according to the assets to be protected, the business context and the potential consequences of exploitation
- Prioritisation strategies
Vulnerability management is the result of a thorough risk assessment, influenced by the methodology adopted and the cyber defence strategy of the organisation. Risks can be assessed either in terms of asset value or in terms of threat scenarios and their potential for exploitation.
Many organisations focus their vulnerability management approach on exploits that are likely to have a critical impact on their activities, while others focus on the criticality of activities performed by automated processes. Once the strategy is in place, it is possible to qualify the criticality of the vulnerabilities using various metrics such as CVSS (Common Vulnerability Scoring System), CVE (Common Vulnerabilities and Exposures), CWE (Common Weakness Enumeration) and EPSS (Exploit Prediction Scoring System) scores. These tools make it possible to increase the relevance of evaluations for better prioritisation, particularly in identifying the most critical weaknesses, so that they can be addressed quickly according to the agreed remediation deadlines.
3. Remediation and patch management : Working closely with the development, infrastructure and systems management teams, the VOC ensures that patches are applied quickly. This may involve applying patches, reconfiguring systems or implementing temporary solutions to avoid incidents.
- Remediation: this aims to correct or completely eliminate a vulnerability. This may include applying patches, updating systems or replacing sensitive software. The aim is to solve the problem once and for all and restore the safety of the environment.
- Neutralisation: this involves removing a threat or disabling a vulnerability so that it cannot be exploited. This may include disabling a service, removing a vulnerable feature or isolating a compromised system. Unlike remediation, neutralisation does not necessarily remove the vulnerability itself, but it does prevent it from being exploited.
- Mitigation: the aim of mitigation is to reduce the risk associated with a vulnerability without eliminating it. This may include measures such as strengthening security controls, segmenting networks, or implementing detection and prevention solutions. The aim is to minimise the potential impact of a vulnerability by making it harder to exploit or less damaging.
4. Monitoring of emerging threats : The VOC constantly monitors cyber threat developments by monitoring security bulletins, public vulnerability advisories and incident reports to stay abreast of new attack vectors and recently discovered vulnerabilities.
- Monitor security bulletins and vulnerability alerts
The VOC closely monitors security bulletins issued by major software vendors (such as Microsoft, Oracle, etc.) as well as public vulnerability alerts issued by organisations such as NIST, CERT and threat intelligence platforms. These sources provide valuable information about recently discovered vulnerabilities, their potential impact and recommended mitigations.
At the same time, the VOC analyses incident reports of real attacks on businesses or critical infrastructure. This approach makes it possible to closely monitor the new techniques used by cybercriminals, such as the exploitation of zero-day vulnerabilities or the advanced methods used by advanced persistent threats (APTs). With this knowledge, the vulnerability management strategy can be adjusted in real time to deal with emerging threats. Cyber posture and the importance of threat intelligence.
An organisation’s cyber posture is heavily influenced by threat intelligence. This information is central to the ability to prioritise security measures according to the most relevant threats to the organisation. Several key elements shape this posture:
- Socle of vulnerabilities
The VOC must have a thorough understanding of the level of vulnerability to which the systems are exposed. This includes regular analysis of the level of exposure, particularly for critical assets such as Single Points of Failure (SPOF) and services exposed to the Internet. This allows remediation efforts to be focused on the vulnerabilities that pose the greatest risk. - APT and exploitation of vulnerabilities
APT groups use advanced techniques to exploit vulnerabilities in critical systems, often unknown or uncorrected. The VOC monitors these threats through intelligence reports that describe the attack methods, tools used, and systems targeted. This allows us to better understand the specific vulnerabilities being exploited by these bad actors and to adjust our priorities to quickly address the most critical vulnerabilities.This information allows the VOC to refine the prioritisation of vulnerabilities, taking into account not only the severity of a vulnerability (based on CVSS scores), but also the likelihood of its being exploited in the context of current threats. For example, an error that is considered moderate by its score could be prioritised if it is actively exploited by a PTA in the organisation’s sector or region. - Integration of bug bounty programs
Integrating bug bounties into the VOC strategy enables a proactive approach to vulnerability management. Rather than being limited to the bugs found by scanning tools, these programs extend the scope of detection by including the perspective of external attackers.
5. Researchers involved in bug bounty programs are often able to find zero-day vulnerabilities in vulnerable areas such as web applications or internet services. These undocumented vulnerabilities can pose a significant risk to the organisation. By participating in these programs, the organisation can quickly identify critical vulnerabilities before they are exploited by malicious attackers.
6. Awareness and training: The VOC also has a training role, raising employee awareness of the risks associated with vulnerabilities and training IT teams in good security practices. This includes organising regular programs to ensure that everyone follows the appropriate safety protocols.
- Continuing education and awareness programs
VOC offers regular internal training programs with a particular focus on IT teams and business functions. These sessions cover :- La sensibilisation aux cyber-risques : explication des menaces liées aux vulnérabilités (exploits, ransomwares, etc.) pour aider les utilisateurs à reconnaître et à signaler tout comportement suspect.
- Raising awareness of cyber risks: explaining the threats associated with vulnerabilities (exploits, ransomware, etc.) to help users recognise and report suspicious behaviour.
- Training in good security practices: highlighting the protective measures to be taken on a daily basis (software updates, access management, etc.) in order to limit the risks of exploitation.
- Regularly update security protocols: Ensure that each team is aware of the latest procedures and technologies to remediate vulnerabilities.
- Sharing of prioritisation bulletins and operational scenarios
- La sensibilisation aux cyber-risques : explication des menaces liées aux vulnérabilités (exploits, ransomwares, etc.) pour aider les utilisateurs à reconnaître et à signaler tout comportement suspect.
The VOC also plays a central role in internal communication with the other cybersecurity entities, in particular the SOC (Security Operations Centre) and the CERT (Computer Emergency Response Team). To enhance threat detection and minimise false positives, the VOC :
- Distributes vulnerability prioritisation bulletins, enabling the SOC and CERT to better focus their efforts on the most critical vulnerabilities.
- Shares exploitation scenarios based on identified vulnerabilities, which are used to refine indicators of compromise (IOC) detection, increasing the responsiveness of defence teams and their ability to identify real attacks.
- Collaboration with government entities and partners
The VOC does not limit itself to internal collaboration, but also works with government bodies such as CERT-FR in order to :
- Share threat and vulnerability information to strengthen national and sectoral security.
- Coordinate joint responses to critical incidents, providing a consolidated line of defence against nation-state threats or sophisticated cyber criminals.
- Training of the business functions and updating of reference systems
Another key role of the VOC is to make business teams aware of the importance of proactive risk and safety management. This means :
- Risk management training: Training in the skills required to carry out risk assessments of their own perimeter and critical assets. This includes the importance of keeping the CMDB (Configuration Management Database) and repositories up to date, which is essential for correctly identifying vulnerabilities and planning their remediation.
- Resource and time optimisation: By encouraging organisations to keep assets and configurations up to date, the VOC can improve its ability to respond quickly to incidents and remediate vulnerabilities, while reducing the burden on its teams.
Technologies and tools used by the VOC
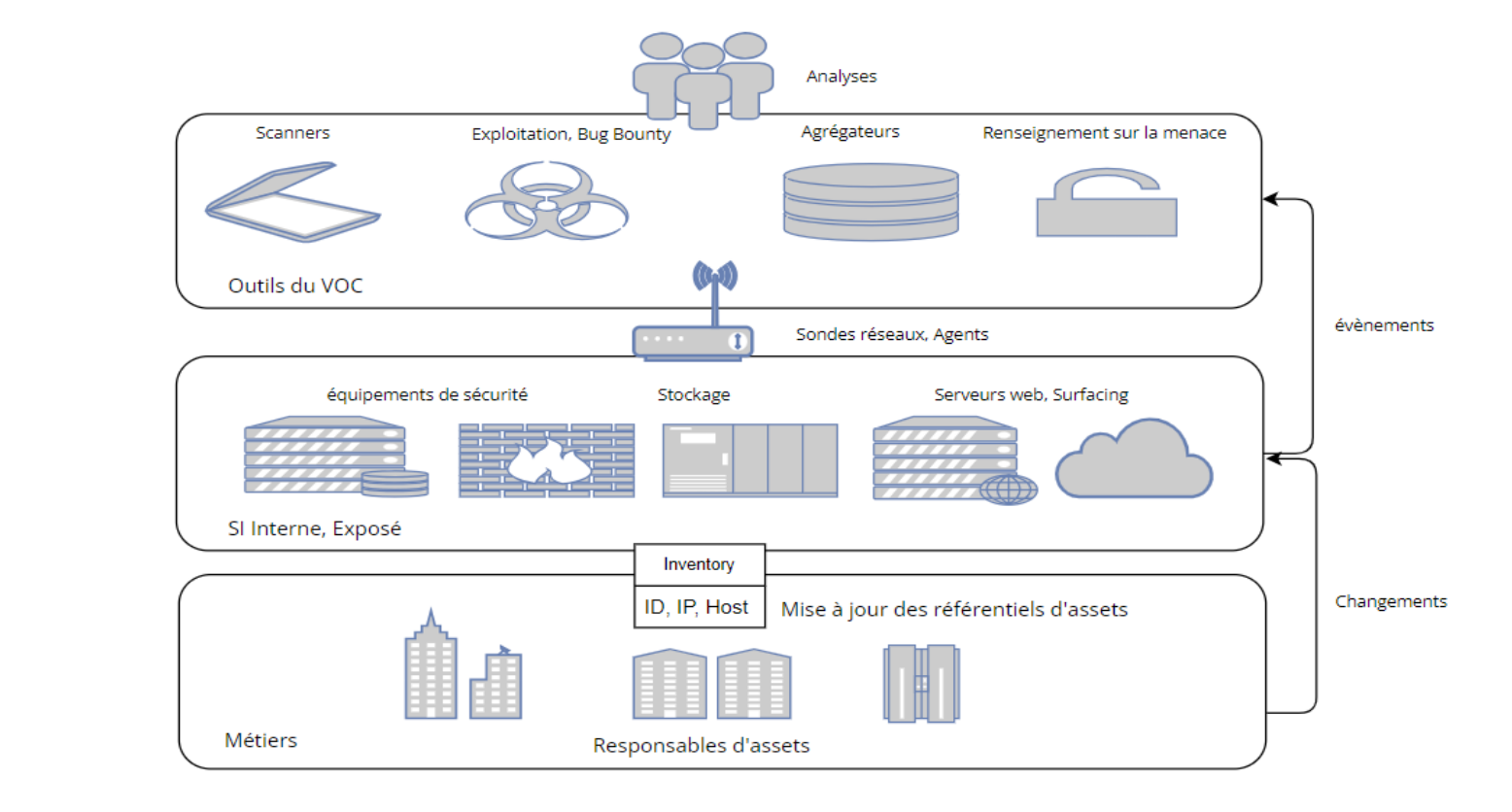
The VOC relies on a range of advanced tools and technologies to detect and remediate vulnerabilities. The most important ones are :
- Vulnerability management systems : these platforms regularly analyse IT assets to identify security vulnerabilities.
- Static and dynamic code analysis tools : these examine the source code of applications to identify vulnerabilities before they go into production.
- Threat Intelligence Platforms (TIP – CTI) : these platforms gather information on threats, emerging vulnerabilities and global incidents, enabling the VOC to adapt its response in real time.
- Patch automation tools : these systems facilitate the rapid deployment of patches and updates across multiple systems, ensuring effective protection against vulnerabilities.
Why is the VOC essential today ?
In a context where cyber-attacks are becoming increasingly complex and frequent, it is essential for organisations to move beyond simply reacting after an incident has occurred. The VOC enables a proactive cybersecurity strategy by identifying vulnerabilities before they are exploited. This significantly reduces the risk of costly incidents and negative impact on the organisation’s reputation.
In addition, with the advent of regulations such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, companies are now required to rigorously protect user data. The VOC plays a crucial role in ensuring compliance with these legal obligations by making sure that systems and applications remain secure at all times against security breaches.
The role of the VOC: more than a technical mission
The VOC is designed to identify, analyse and fix IT vulnerabilities before they are exploited by malicious actors. While a Security Operations Centre (SOC) focuses on real-time incident management, the VOC takes a preventative approach, addressing potential vulnerabilities before they become critical.
But the scope of the VOC is not limited to a purely technological function. It is also involved in strategic decisions on risk management and the allocation of resources to ensure the security of the organisation.
The management challenges of the VOC
Establishing and managing a Vulnerability Operations Centre (VOC) presents a number of management challenges. The first is to establish a true culture of cybersecurity within the organisation. The VOC must work closely with various departments, such as development, operations and human resources. Smooth communication and effective coordination between these teams is essential to ensure that vulnerabilities are not only identified, but also addressed quickly and effectively.
Another management challenge is the commitment of managers to vulnerability management. Senior executives (CEO, CFO, CIO) need to understand the issues associated with security vulnerabilities and actively support initiatives to reduce them. This often requires strategic decisions, such as allocating resources, prioritising security measures and integrating risk management into the overall governance of the business.
Finally, an effective VCC relies on a skilled team of cybersecurity experts. This requires recruiting, training and retaining specialist talent – a major challenge in an environment where the IT security skills shortage is becoming increasingly worrying.
Political and regulatory issues
Cyber-attacks are not only a threat to the stability of businesses, but have also become a major concern at the political level. Legislative pressure is increasing, with regulations such as the GDPR in Europe and the CCPA in California requiring companies to protect sensitive data. The role of the VOC is therefore critical in preventing vulnerabilities from leading to data breaches that could expose the organisation to legal sanctions and heavy fines.
The VOC contributes directly to regulatory compliance by continuously monitoring systems and ensuring that necessary corrective actions are quickly implemented to meet regulatory requirements. In sectors such as finance and healthcare, where regulators impose rigorous cybersecurity standards, VOC is becoming an essential pillar to avoid penalties and maintain stakeholder confidence.
Budgetary challenges: finding the right balance between costs and performance
The establishment and management of a Vulnerability Operations Centre (VOC) requires significant investment and raises important budgetary issues. Organisations need to determine how much of their budget to allocate to proactive vulnerability management, while balancing this expenditure against other strategic priorities.
It is essential for management to measure the return on investment (ROI) of cybersecurity spending, taking into account not only the initial cost, but also the savings achieved by preventing attacks. Organisations that fail to invest sufficiently in a VOC leave themselves open to costly cyber-attacks that can disrupt their operations, damage their reputation and cause significant financial loss.
The VOC must prove its effectiveness by demonstrating that the detection and correction of vulnerabilities helps to avoid potentially much more costly incidents. This requires the implementation of key performance indicators (KPIs) to assess the effectiveness of VOCs and justify these investments to decision makers.
Conclusion :
The Vulnerability Operations Centre (VOC) is more than just a technical function: it is now a key element of risk management strategy, regulatory compliance, budgetary decisions and governance challenges. Today, an organisation’s ability to anticipate, control and reduce vulnerabilities is critical to remaining resilient in the face of cyber threats.
In a world where cybersecurity is a key factor for success, the VOC is positioned as an essential lever to ensure the sustainability and competitiveness of organisations. Based on a long-term strategic vision and optimised management of human, financial and technological resources, the VOC enables proactive identification of vulnerabilities and targeted management of threats. As cyber-attacks become more complex and frequent, the VOC is essential to ensure solid and long-lasting protection.
Mohamed Aïssou

